
Creating authentic forest landscapes: essential techniques for realistic foliage in exploration games
Techniques for Designing Realistic Forest Landscapes Designing a realistic forest landscape requires meticulous attention[…]

Mastering Secure Reverse Proxies: Your Ultimate Guide to Leveraging Traefik with Docker
Understanding Reverse Proxies A reverse proxy is a type of server that acts as[…]

Essential Tactics for Protecting Your AI-Powered Customer Support Framework
Overview of AI-Powered Customer Support Vulnerabilities Diving into the AI-driven systems that power customer[…]

Key Components for Developing an Effective Digital Transformation Strategy for UK Enterprises
Leadership Alignment in Digital Transformation Achieving successful digital transformation in any organisation fundamentally hinges[…]

Supercharge Your Network: The Comprehensive Handbook for Setting Up Your TP-Link TL-SX1008 10GbE Switch
Overview of the TP-Link TL-SX1008 10GbE Switch The TP-Link TL-SX1008 is a cutting-edge solution[…]

Comprehensive Guide: Setting Up a Secure Cisco AnyConnect VPN for Your Enterprise Network
Overview of Cisco AnyConnect VPN The Cisco AnyConnect VPN is a robust remote access[…]

Key Tactics for Seamless Hybrid Cloud Integration in the UK Financial Services Industry
Understanding Hybrid Cloud Integration in Financial Services Hybrid cloud integration is redefining how financial[…]
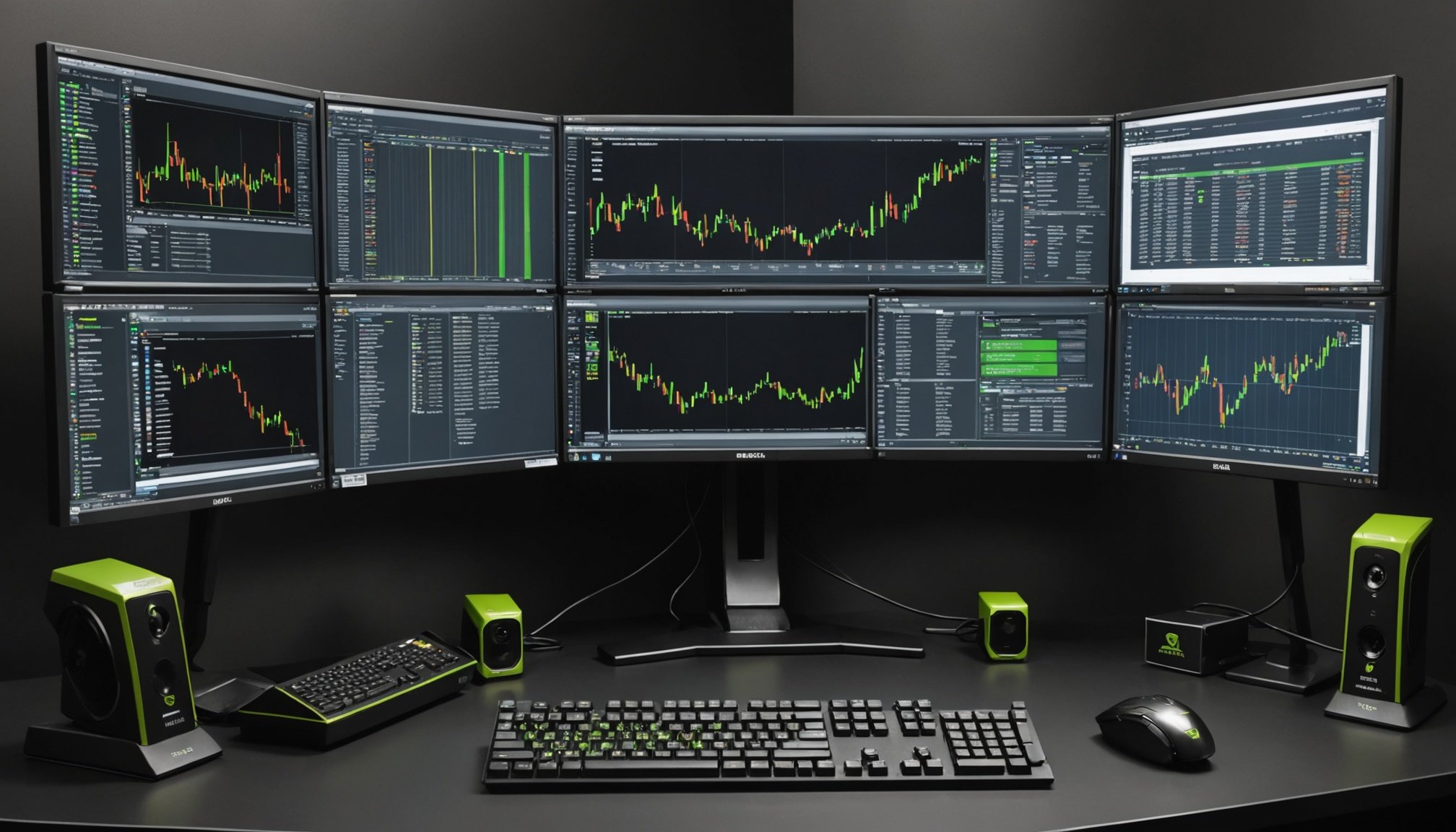
Revolutionize Your Trading Experience: Maximizing Performance with Advanced Multi-Monitor Configurations Using NVIDIA Quadro P2000
Understanding Multi-Monitor Configurations for Trading Multi-monitor trading setups have become indispensable tools for enhancing[…]

Mastering API Endpoint Security: Implementing OAuth 2.0 in Your Flask Application
Understanding OAuth 2.0 Fundamentals OAuth 2.0 is a pivotal authorization framework in the realm[…]

Essential Strategies for Building a Robust and Secure Machine Learning Pipeline
Overview of Machine Learning Pipelines Machine Learning Pipelines are essential frameworks that automate the[…]









